Hardware-Level Resilience with Smart Card + Secret Share
The key to security isn’t where it’s stored — it’s how it’s created and shared.

The key to security isn’t where it’s stored — it’s how it’s created and shared.
All in one solution for my crypto needs
Split the Key. Multiply the Security.
Smart Cards with CSTRNG: Randomness You Can Trust
Our smart cards are equipped with Cryptographically Secure True Random Number Generators (CSTRNG) — compliant with global standards such as FIPS 140-3 and Common Criteria EAL5+.
- Hardware-based entropy from physical noise sources
- Non-predictable and non-reproducible outputs
- Ideal for generating private keys, PINs, recovery seeds
- Immune to software-based RNG manipulation
Unlike pseudo-random software methods, CSTRNG ensures that each key is truly unique, non-reproducible and quantum-resistant.
Shamir’s Secret Sharing: Don’t Back Up — Divide
Instead of storing a key in one place, Shamir’s Secret Sharing Scheme (SSSS) divides it into multiple encrypted “shares.” Only a defined quorum is needed to reconstruct the original secret.
- e.g. Split into 5 shares, recoverable with any 3
- Each share is meaningless on its own
- No single point of failure
- Shares can be distributed across multiple cards, people, or locations
This enables decentralized key recovery, collaborative custody, and enhanced survivability in the event of loss, theft, or disaster.
Ideal for Wallets, DAOs & High-Security Environments
This model is perfect for:
- Hardware wallet backups without cloud dependency
- DAOs or treasuries requiring multi-party access control
- Enterprise-grade self-custody with tamper-proof hardware
- Emergency recovery kits distributed across geographic zones
It’s the gold standard for anyone who can't afford to lose — or expose — their private keys.
Integrated Security & Developer Options
- Compatible with JavaCard, NFC Smart Cards, and HSMs
- Native support for mTLS, PGP, ECDSA, and key wrapping
- APIs for secret splitting, verification, and secure reconstruction
- Can be combined with biometric MFA, stealth address, or secure enclave logic
Smart cards become not just secure storage — but active participants in secure computation.
Not all security is in the cloud. Some of it fits in your pocket — and belongs only to you.
With Smart Cards, CSTRNG, and Secret Sharing, you're protected by the physics of randomness and the logic of trust.
Start Your Crypto Journey Today
Join a growing community of digital pioneers. Manage your assets, explore innovative tools, and unlock the potential of cryptocurrency with ease.
Explore the Key Features That Power Your Crypto Journey
Explore our suite of premium features and services designed to simplify and enhance your overall cryptocurrency experience.
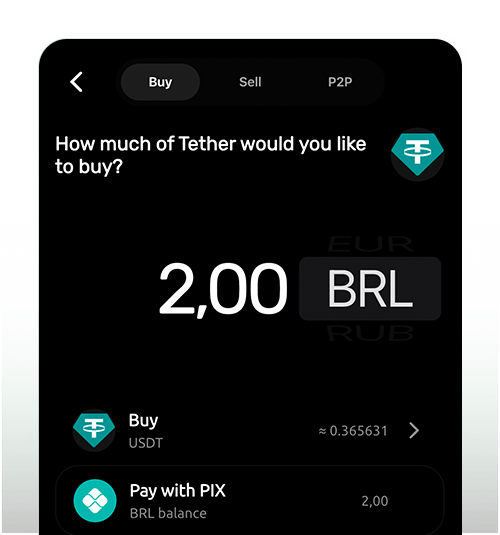
Simple On-Ramp
Effortless crypto onboarding through local payment methods like Pix, no complex exchanges or middlemen
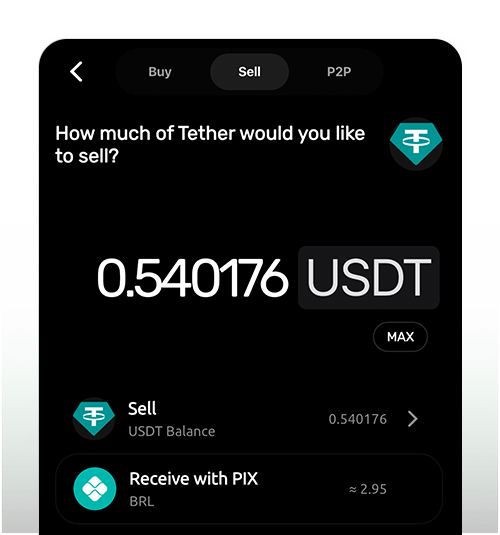
Instant Off-Ramp
Convert your crypto to local currency and withdraw instantly using trusted payment methods like Pix. Immediate access, zero friction.
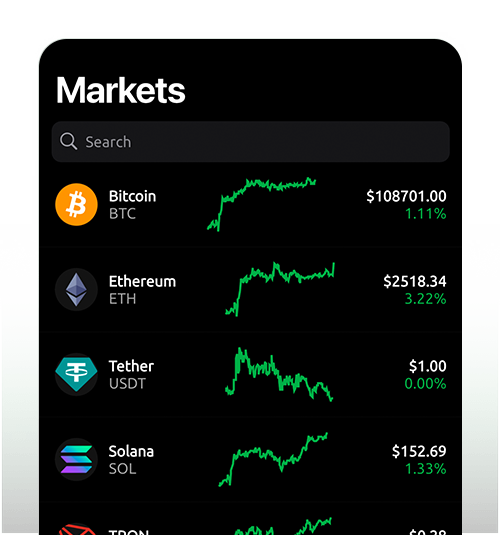
DeFi Solutions
Access the decentralized financial tools you need to grow your wealth. Grow and move your wealth freely.

P2P Easy: Fast & Direct
Peer-to-peer trading of crypto and stablecoins, fast, secure, and borderless.

